In today's digital age, the necessity to transform cybersecurity within organizations is paramount due to the escalating complexity and sophistication of cyber threats. We are tireless advocates for a holistic approach that integrates cybersecurity seamlessly into the organization's structure, processes, and culture. Recognizing that cybersecurity is not just a department or set of tools, but a fundamental aspect of enterprise resilience, we leverage multiple tools to help bridge the gap between cybersecurity and broader organizational functions.
Holmes Cybersecurity Transformation encompasses people, processes, technology, strategy, partners, and overall maturity. This set of tools does not take the place of the normal essential programs that are usually on-going in cybersecurity programs, such as vulnerability scans, process reengineering, technology and tools modernizations, and review of controls against various compliance standards. Unlike some of these traditional isolated approaches, this comprehensive strategy aims to address systemic vulnerabilities by considering the entire organizational ecosystem.

-
Cybersecurity Organizational Maturity Scan:
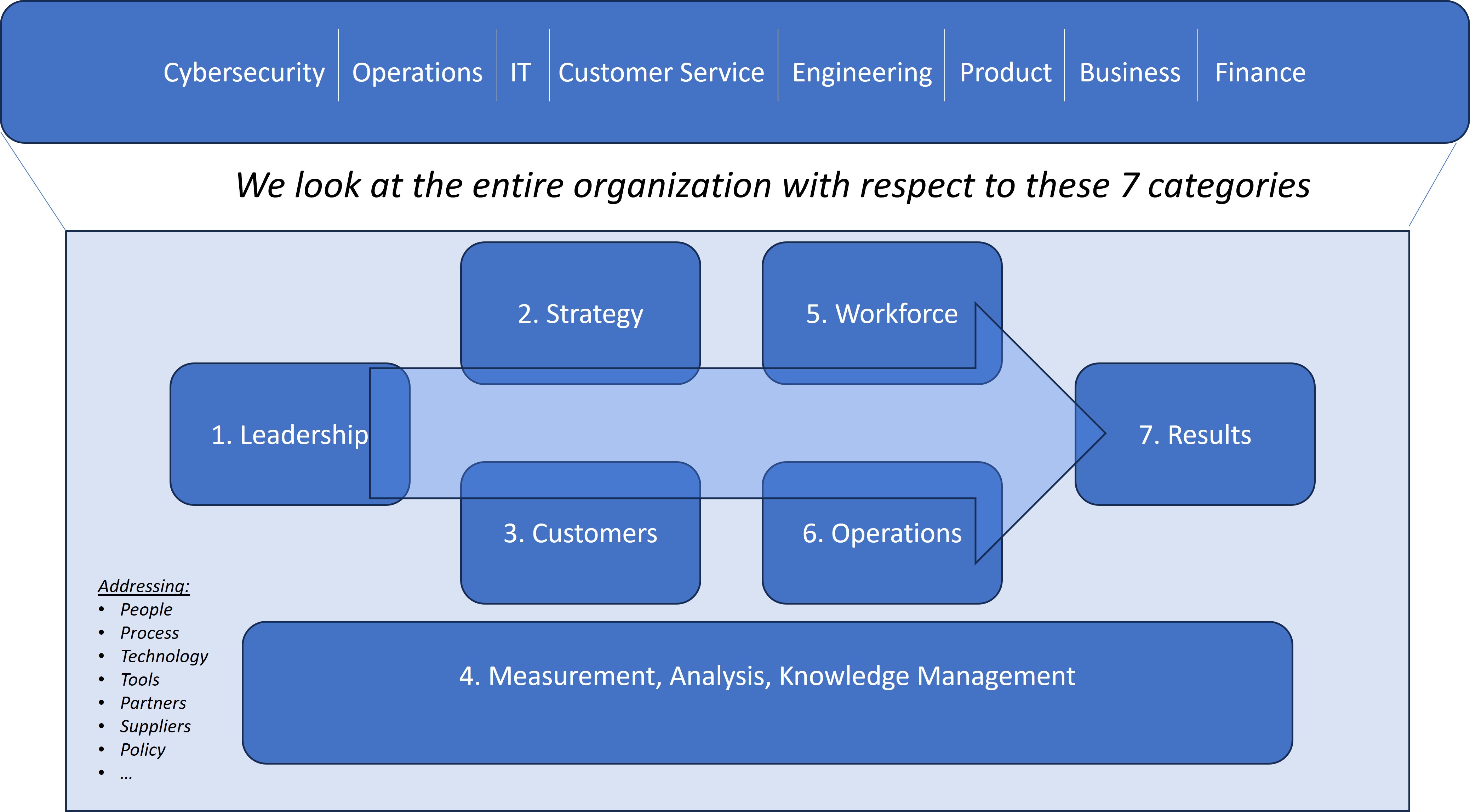
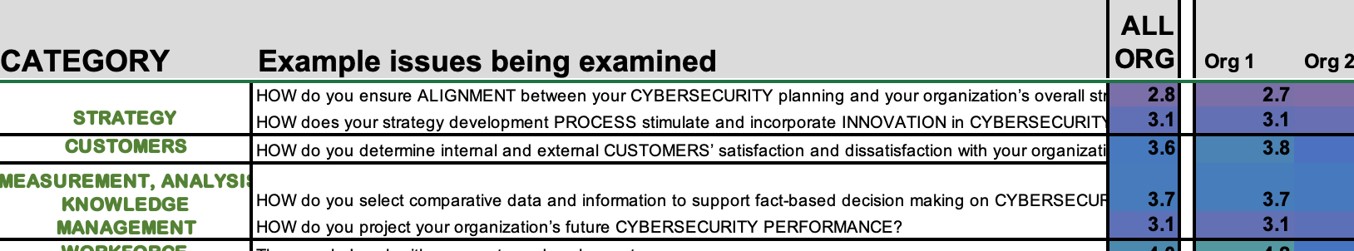
This initial component enables the enterprise to evaluate cybersecurity risk management across the organization, emphasizing both vertical and horizontal alignment. By assessing leadership, policies, behaviors, operations, and results, COMS provides a holistic view, enabling prioritization, investment decisions, and identification of strengths and weaknesses. We use an organizational assessment tool and engage with people across the organization to look at Leadership, Strategy, Customers, Measurement/Analysis/Knowledge, Workforce, Operations, and Results. These results are compiled so that we can identify areas of opportunities for more maturity and hence areas of potential vulnerability that can be factored into the roadmap.
- Systems Engineering Analysis and Vulnerabilities (via STPA):
Building on systems engineering principles, this analysis process extends beyond examining individual vulnerabilities to analyze systemic vulnerabilities across the enterprise ecosystem. Using Systems Theoretic Process Analysis (STPA), it identifies interactions between subsystems, people, processes, and technologies, facilitating a more unified approach to risk management and alignment with business objectives. The power of this technique is that provides a consistent and reliable approach to decomposing large, complex systems and interactions. Holmes and Associates is working with the creator of STPA-Sec, the variation of STPA that focuses on cybersecurity.
This methodology and its variants are used in industry and across the military. In particular, in the Department of Defense (DoD) 2020 DOT&E Annual Report, the DoD wrote this about using STPA-Sec on the Ground Based Strategic Deterrence (GBSD) Program:
"The use of STPA-Sec by the GBSD program was indicated by the Office of the Director, Operational Test and Evaluation (DOT&E) as a contributing factor in reducing cybersecurity and schedule risks."
Holmes and Associates is working directly and closely with the creator and world's leading expert on STPA-Sec, Dr. William Young, PhD, Retired Colonel from the US Air Force. We combine Dr. Young's thought leadership with our knowledge and thought leadership on organizational transformation, organizational change, and with our experience running IT and Cybersecurity organizations. An organization that adopts STPA-Sec will be able to systematically identify hazards and vulnerabilities across its complex environment containing systems, people and processes.
-
Cybersecurity Maturity Simulation and Predictive Modeling:
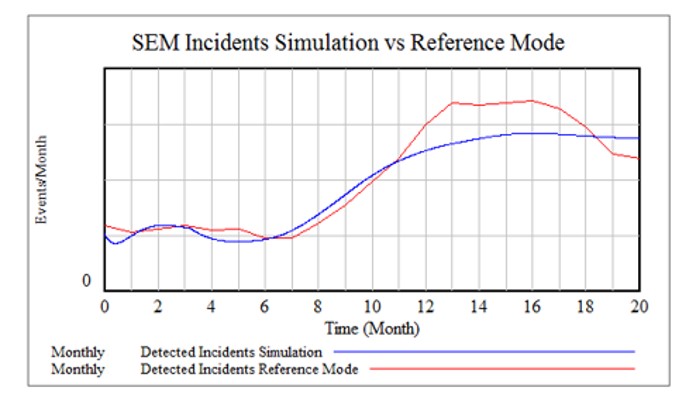
Recognizing the inadequacy of depending only on retrospective analysis, this component utilizes advanced modeling and simulation techniques to forecast future cyber risk management strategies' effectiveness. By simulating scenarios in a quantitative systems dynamics model, leaders can make informed decisions on investments in staffing, engineering, training, and productivity tools, optimizing resource allocation based on predicted outcomes. This approach was shown to be extremely accurate in predicting trends in adversarial behaviors in combination with decisions on resource allocations and investments for a large Fortune 500 financial institution. The tool then allows a what-if investment scenarios that can lead to rational, optimized business decisions that take into account the many tradeoffs. For example, shifting investment from reactive to proactive can help with response but may lead to the invitation to more adversarial attacks. The simulation uses past history of these complex interrelationships to gauge the tradeoffs.
This portfolio complements traditional cybersecurity assessments and planning activities. By combining traditional means such as compliance assessments, technology evaluations, with these new approaches, organizations can improve their strategic planning and roadmap to achieve maximum impact and sustainable cybersecurity results.
